Spear Phishing

How Does Spear Phishing Work?
Spear phishing attacks typically follow these steps:
- Reconnaissance: Attackers gather information about their target from social media, company websites, or other publicly available sources.
- Crafting the Message: Using the collected data, they create a convincing email, text, or message that appears trustworthy.
- Delivery: The message is sent, often containing a malicious link or attachment.
- Exploitation: If the victim takes the action or click, the attacker gains access to sensitive information or infects the system with malware.
Where to Add Picture: Add a flowchart illustrating these steps with icons for each phase (e.g., magnifying glass for reconnaissance, email icon for delivery).
Common Tactics Used in Spear Phishing
- Personalized Messages: Using names, job roles, or recent activities to gain trust.
- Spoofed Email Addresses: Sending emails that look like they come from trusted sources.
- Urgent Requests: Creating a sense of urgency to pressure victims into acting quickly.
- Malicious Attachments: Including documents or files that install malware when opened.
How to Identify Spear Phishing Attempts
- Look for inconsistencies in email addresses or URLs.
- Be cautious of unsolicited messages with urgent requests.
- Verify the sender’s identity before taking action.
- Avoid clicking on links or downloading attachments from unknown sources.
- Download software and program from valid sources.
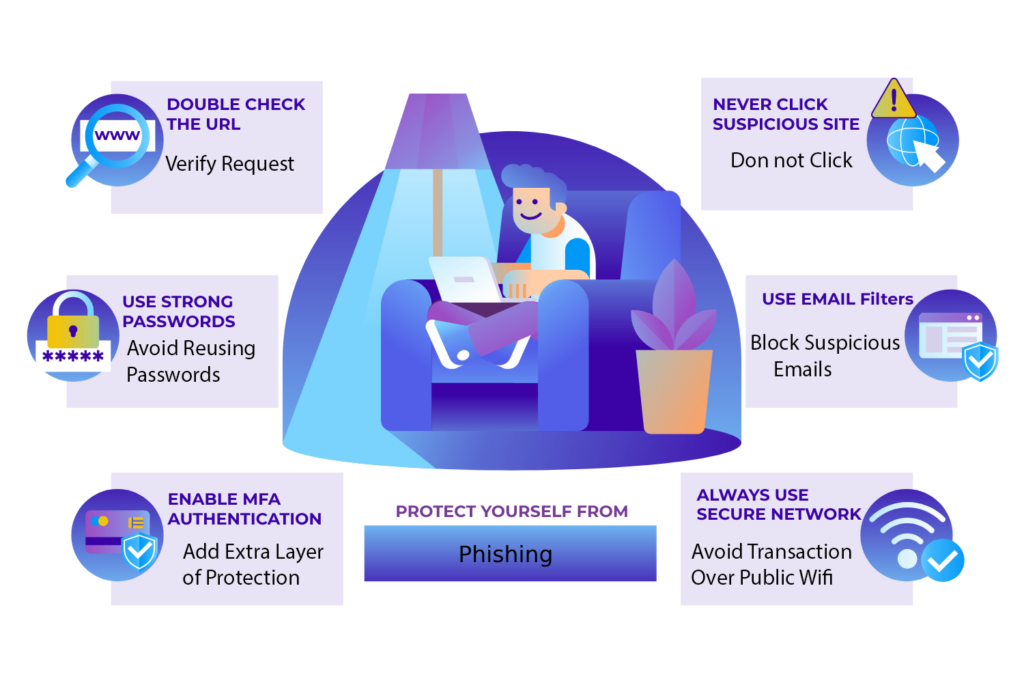
How to Protect Yourself Against Spear Phishing
- Enable Multi-Factor Authentication (MFA): Adds an extra layer of security to your accounts.
- Educate Yourself and Others: Conduct regular training to recognize phishing attempts.
- Use Email Filters: Block suspicious emails before they reach your inbox.
- Verify Requests: Always double-check requests for sensitive information through another communication channel.
- Keep Software Updated: Ensure your systems have the latest security patches.
What to Do If You’ve Been Targeted
- Do not interact with the email further.
- Report the phishing attempt to your IT or security team.
- Change your passwords immediately if you suspect your credentials have been compromised.
- Monitor your accounts for any unauthorized activity.
Credit and Resources:
- Image Credit- Designed by Freepik. Link for website (https://www.freepik.com/).